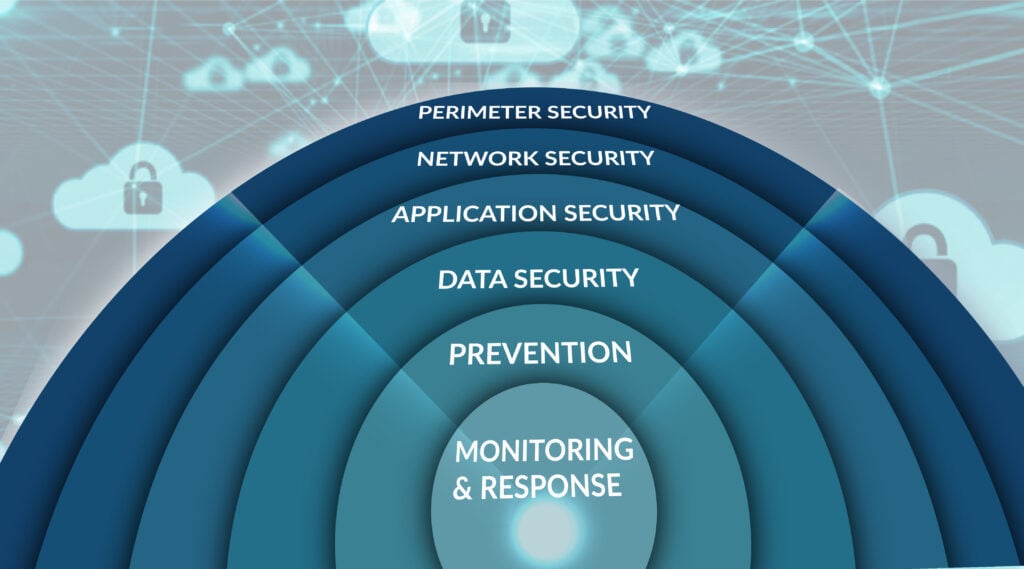
SOC and MDR’s reduce cybersecurity risk. There is no doubt that these solutions play a critical role in mitigating exposure. Combined, the impact these solutions have on an organization’s cyber defenses cannot be exaggerated. A complete, multi-layered cybersecurity plan should include a Security Operations Center (SOC) coupled with Managed Detection & Response.
A SOC’s importance has risen as data breaches and ransomware become increasingly real risks for all organizations no matter their size or line of business. In fact, most cybersecurity insurance underwriters now require a SOC with MDR support to be fully operational to even offer or “write” a policy. Today, the sophisticated, socially-engineered attacks do not discriminate – cyber criminals are diligently on-the-prowl to find and exploit network vulnerabilities. That is why building a strategy against cyber threats is a key concern for all organizations. Traditional cyber technologies like anti-virus or anti-malware alone are not strong enough to thwart modern adversaries. To reduce risk, aggressive, proactive protections are a necessity in today’s hostile cyber landscape.
What is clear is the need to have both proactive and preventative measures. This mindset is starting to guide more organizations toward adding a Security Operations Center (SOC) solution as part of multi-layered approach to minimize cyber risk. And limiting your organizations risk of data loss, and interruption of business operations are the primary drivers of investing in cyber security solutions.
SOC – Defined
A Security Operations Center (SOC) is a centralized hub that combines dedicated security analysts, processes, and technology to continuously monitor an organization’s security posture. SOCs are focused on using telemetry measured from across an organization’s IT infrastructure and assets to prevent, detect, assess, and respond to cybersecurity incidents.
SOC – Key Deliverables
All SOC solutions are built differently, and many providers allow organizations to select the specific services that best serve their needs.
Below are some of the key solutions a high-quality SOC delivers:
• 24/7/365 Proactive Monitoring: A SOC should scan your networks 24/7/365 through proactive behavior monitoring and analysis. When an anomaly is detected or evidence of suspicious activity is discovered, the SOC investigates immediately. This means your organization increases the probability to stop an attack. Additionally, it’s widely-known that cyber attacks are orchestrated after traditional working hours to maximize potential success. With 24/7/365 SOC monitoring, in-house IT staff are immediately alerted, and have the peace-of-mind that every threat is fully investigated and resolved. No threat falls-through-the-cracks.
• Threat Response – First Line of Defense: Time is the most crucial factor when it comes to protecting your data. And a these services shorten the time from detection to remediation. This first line of defense that a SOC plays is crucial. By immediately taking remediation action we stop the threat from further infiltration into the network.
• Incident Recovery: In the event of a security event, GBS and the chosen SOC partner, will work with you during the incident response process by providing expertise and guidance. This cyber resource team can move quickly to restore systems back to operational status, and execute full recovery actions.
• Alert Fatigue: Alert fatigue among the IT community is real. Remember the famous fable, “The Boy Who Cried Wolf”? That’s a great Alert Fatigue analogy.
For companies that rely on SEIM logging in-house, your IT resources can become overwhelmed with false positives. The result – legitimate notifications are missed or not remediated. GBS and leading SOC partners, like Blackpoint Cyber or Arctic Wolf provide this service and sift through the incoming alerts and efficiently assess whether immediate action is needed.
• Post-Incident Investigation: Post-incident work is just as important as catching and eliminating the threat. A SOC performs a root cause analysis and investigation to find out how and why the event occurred and then reports back with clear action items. Post-incident investigations are also important for settings lessons learned benchmarks for how better to prevent similar events from occurring in the future.
• Asset Discovery & Management: SOCs manage two main categories of assets: the devices, and applications of the organization they are defending. In SOC operations, having full visibility and control is key. This allows them to build a complete map of all available assets on the networks and be able to manage any weak or blind spots. With a complete view of all the endpoints, software, servers, services, SOCs can stay on top of the nature of traffic flow and monitor the environment for anomalies.
•Activity Log Collection: As the SOC collects, maintains, and reviews all network activity, it allows the SOC to acquire a baseline snapshot of what normal network operations look like. This is significant for you, the client and the SOC, as it allows the team to better locate threats, malicious files, and asset changes. Compiling activity logs is critical. Logs are one of the keys for remediation and forensic analysis.
• Compliance Strategy: Compliance audits ensure that organizations handling sensitive information are held to a standard set of rules and regulations. Should a breach occur, being compliant can shield the organization from reputational damage as well as severe legal and financial ramifications.
SOC + MDR Reduce Cybersecurity Risk
It is no doubt that, from a security strategy standpoint, having a SOC means responding faster, minimalizing damages, and safeguarding data and business continuity. However, is there a way to level up your cybersecurity strategy for the long-term game?
SOC: Firm Up Your Defense
Adding a SOC solution will advance your fight against modern, advanced cyber threats. Adding SOC services to a Managed Service partnership ensures a robust cybersecurity foundation staffed with security experts with experience managing ever-evolving cyber adversaries.
Ultimately, a SOC allows your organization to operate while being confident that cyber threats are being identified and prevented in real-time. Regardless of how many endpoints, networks, assets, or locations an organization spans, SOCs provide a centralized view to ensure that they are monitored and performing as needed.
Today, SOC-as-a-Service is a model that gives organizations the ability to outsource threat detection and incident response work. SOC-as-a-Service is external to your current IT operation, and offers cybersecurity services such as monitoring, detection, and investigation for threats in that organization’s environment. With a dedicated SOC, response times to threats are immediate – giving you peace-of-mind knowing all threats are being addressed and not falling through the cracks.
Managed Detection & Response (MDR): Build Your Offense
To develop the most comprehensive solution, SOC services often included Managed Detection Response (MDR) services. As the SOC collects and monitors various data sources within the organization, it is the MDR that adds context and makes the information more valuable and actionable within the overall threat management process.
With MDR and SOC services clients receive threat monitoring, network visualization, traffic analysis, and endpoint security 24/7/365. Managed Services solution professionals, like GBS, are able to orchestrate and manage the totality of a multi-layered cyber security plan – a plan that can include SOC and Managed Detection and Response services.
For a no-cost consultation. Contact GBS Managed Services 859.491.5900 or https://www.gbs-inc.com/contact/