Beware of cybercriminals using conversation hijacking to steal money and sensitive personal information.
In recent months, Barracuda researchers have seen a sharp rise in domain-impersonation attacks used to facilitate conversation hijacking. An analysis of about 500,000 monthly email attacks shows a 400-percent increase in domain-impersonation attacks used for conversation hijacking. In July, there were about 500 of this type of domain-impersonation attack in the emails analyzed, and that number grew to more than 2,000 in November.
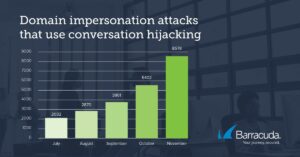
While the volume of conversation hijacking in domain-impersonation attacks is extremely low compared to other types of phishing attacks, these sophisticated attacks are very personalized, making them effective, hard to detect and costly.
Here’s a closer look at the growing threat of conversation hijacking in domain-impersonation attacks, along with tips to help protect your business.
Conversation Hijacking
Cyber thugs insert themselves into existing business conversations or initiate new conversations based on information they’ve gathered from compromised email accounts or other sources. Conversation hijacking is typically, but not always, part of an account-takeover attack. Attackers spend a great deal of time reading through emails and monitoring the compromised account to understand business operations and learn about deals in progress, payment procedures, and other details.
These attacks rarely use the compromised accounts for conversation hijacking. Instead, attackers use email-domain impersonation. They leverage information from the compromised accounts, including internal and external conversations between employees, partners, and customers, to craft convincing messages, send them from impersonated domains, and trick victims into wiring money or updating payment information.
Details of an Attack
To execute conversation-hijacking attacks, cybercriminals use domain impersonation, including typo-squatting techniques, such as replacing one letter in a legitimate URL with a similar letter, or adding an unnoticeable letter to the legitimate URL. In preparation for the attack, cybercriminals will register or buy the impersonating domain.
Domain impersonation is a very high-impact attack. It can be easy to miss the subtle differences between the legitimate URL and the impersonated URL.
For example, an attacker trying to impersonate barracudanetworks.com would use a very similar URL:
- barracudanetwork.com
- barracadanetworks.com
- barracudaneteworks.com
- barrracudaneteworks.com
Sometimes, an attacker changes the Top-Level-Domain (TLD), using .net or .co instead of .com, to fool victims:
- barracudanetworks.net
- barracudanetworks.co
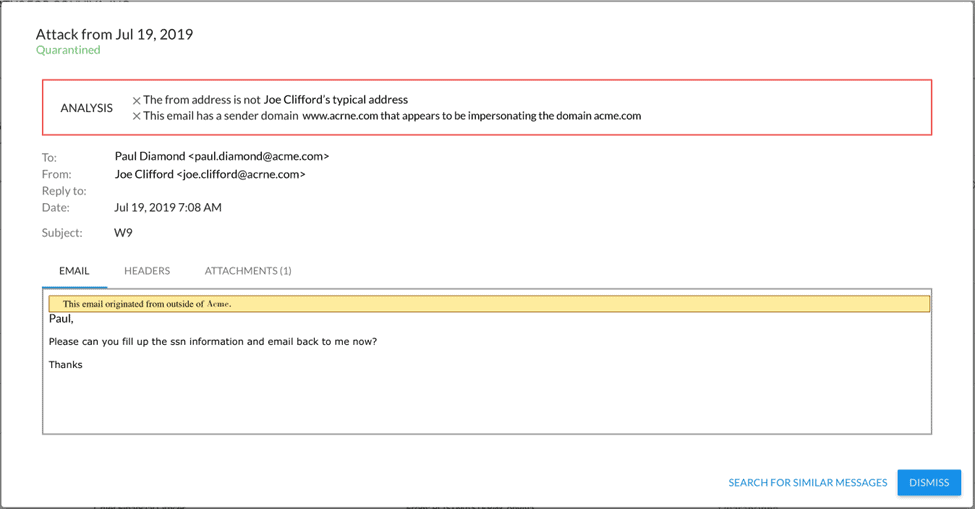
Here’s an example of cybercriminals impersonating an internal domain:
For example, an attacker trying to impersonate barracudanetworks.com would use a very similar URL:
- barracudanetwork.com
- barracadanetworks.com
- barracudaneteworks.com
- barrracudaneteworks.com
Sometimes, an attacker changes the Top-Level-Domain (TLD), using .net or .co instead of .com, to fool victims:
- barracudanetworks.net
- barracudanetworks.co
In other cases, attackers impersonate the external domain of a customer, partner, or vendor:
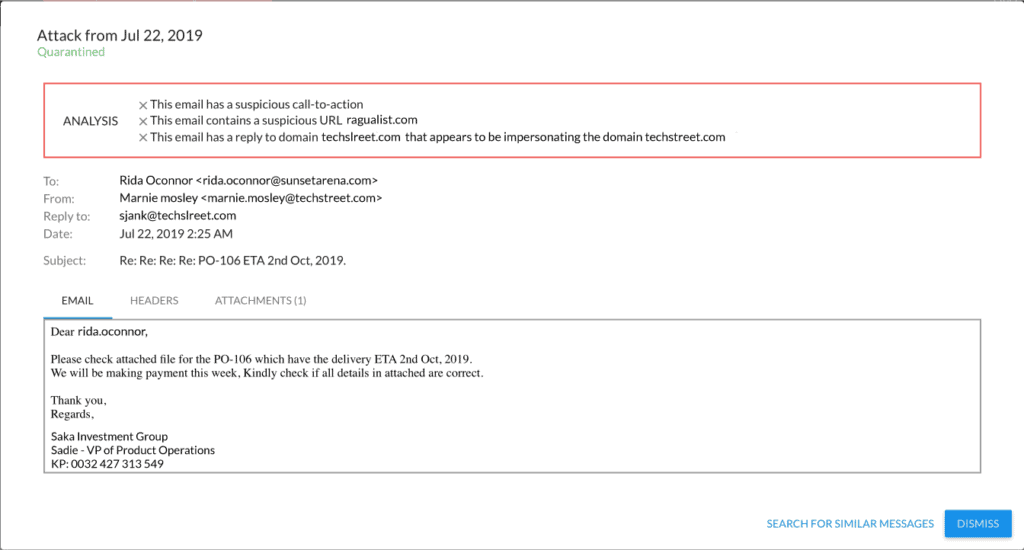
Ultimately, the goal of these attacks is to trick victims into wiring money, making a payment of some kind, or change payment details. Domain impersonation and conversation hijacking require an investment of both time and money from the attacker. From the attacker’s perspective, however, the cost is worth it because these personalized attacks are often more successful at tricking victims than other less sophisticated phishing attacks.
Key Ways to Protect against Conversation Hijacking
To protect your business from conversation hijacking, GBS Managed Security Services deploys a variety of cybersecurity technologies and techniques to protect your organization against falling victim to conversation hijacking:
Train employees to recognize and report attacks
Educate users about email attacks, including conversation hijacking and domain impersonation, as part of security-awareness training. Ensure staffers can recognize attacks, understand their fraudulent nature, and know how to report them. Use phishing simulation to train users to identify cyberattacks, test the effectiveness of your training, and evaluate the users most vulnerable to attacks.
Deploy account-takeover protection
Many conversation hijacking attacks will start with account takeover, so be sure scammers aren’t using your organization to launch them. Use multi-factor authentication to provide an additional layer of security above and beyond a username and password. Deploy technology that recognizes when accounts have been compromised and that remediates in real time by alerting users and removing malicious emails sent from compromised accounts.
Monitor inbox rules, account logins, and domain registrations
Use technology to identify suspicious activity, including logins from unusual locations and IP addresses, a potential sign of a compromised account. Be sure to also monitor email accounts for malicious inbox rules, as they are often used as part of account takeover. Criminals log into the compromised account, create forwarding rules, and hide or delete any email they send from the account, to try to cover their tracks. Keep an eye on new domain registrations that could potentially be used for impersonation through typo-squatting techniques. Many organizations choose to purchase domains that are closely related to their own to avoid the potential fraudulent use by cybercriminals.
Leverage artificial intelligence
Scammers are adapting email tactics to bypass gateways and spam filters, so it’s critical to have a solution in place that uses artificial intelligence to detect and block attacks, including account takeover and domain impersonation. Deploy purpose-built technology that doesn’t rely solely on looking for malicious links or attachments. Using machine learning to analyze normal communication patterns within your organization allows the solution to spot anomalies that may indicate an attack.
Strengthen internal policies
Help employees avoid making costly mistakes by creating guidelines and putting procedures in place to confirm all email requests for wire transfers and payment changes. Require in-person or telephone confirmation and/or approval from multiple people for all financial transactions.
GBS email security experts are here to help secure your organization’s inboxes. Contact us for more information about Barracuda Total Email Protection.


